Electric Grid Cyberattack: An AI-Informed Threat Model
post by moonlightmaze · 2024-11-11T21:34:17.190Z · LW · GW · 0 commentsContents
Author’s note: This post was written during a two-week long research sprint at constellation.org. My analysis represents a preliminary attempt to formulate a detailed AI-cyber threat model of attacks against the energy grid. The conclusions reached here are therefore tentative and I seek further inp... AI is already changing the cyber threat landscape Catastrophic cyberattacks against critical infrastructure Building on Lloyd’s (2015) “Business Blackout” scenario How does the power grid work? How could a cyberattack destabilize the power grid? How a cyberattack could cause >$100B of damage through destabilization of the power grid: direct and indirect approaches. Unresolved questions How do increases in offensive AI cyber capabilities affect this analysis? Conclusion None No comments
Author’s note: This post was written during a two-week long research sprint at constellation.org. My analysis represents a preliminary attempt to formulate a detailed AI-cyber threat model of attacks against the energy grid. The conclusions reached here are therefore tentative and I seek further input from experts to refine and correct my work. I offer special thanks to Luca Righetti from openphilanthropy.org and Matthew van der Merwe from governance.ai for their generosity and rigorous insight.
This post covers the following:
- AI is changing the cyber threat landscape
- Catastrophic cyberattacks against critical infrastructure
- Building on Lloyd’s (2015) “Business Blackout” scenario
- How does the power grid work?
- How could a cyberattack destabilize the power grid?
- How a cyberattack could cause >$100B of damage through destabilization of the power grid: direct and indirect approaches
- Three major attack scenarios causing damages on the order of $100 Billion or more
- Unresolved questions
- How do AI offensive cyber capability increases affect this analysis?
AI is already changing the cyber threat landscape
AI developments over the last two years are heavily shaping global perceptions of national security and cyber threats. In October 2024, the US Presidential administration issued a National Security Memorandum titled Advancing the United States’ Leadership in Artificial Intelligence; Harnessing Artificial Intelligence to Fulfill National Security Objectives; and Fostering the Safety, Security, and Trustworthiness of Artificial Intelligence. The memorandum mandates the US AI Safety Institute (USAISI), National Security Agency (NSA), and other federal agencies evaluate frontier models’ ability to aid offensive cyber operations. Furthermore, the memorandum calls on Department of Defense and Intelligence Community agencies to harness powerful AI systems in furtherance of their national security missions. This undoubtedly includes using frontier AI for offensive cyber operations.
In 2024, OpenAI published two reports detailing Russian, Iranian, Chinese, and North Korean cyber threat actors' use of the company’s proprietary AI models in offensive cyber operations tasks. These actors used OpenAI’s Large Language Models (LLM) to supplement their reconnaissance, social engineering, vulnerability research, attack tool scripting, anomaly detection evasion, and post compromise activity in furtherance of their ongoing campaigns.
In their most recent system card evaluating the o1 model’s offensive cyber capabilities, OpenAI showed the model could independently complete certain competitive hacking tasks called Capture the Flag (CTF) challenges. Even with safety guardrails in place, o1-preview completed 26.7% of high-school level and 2.5% of professional level challenges; o1-mini completed 28.7% of high-school level and 3.9% of professional level challenges. While these results show that o1 independently does not reach the capability or sophistication of talented or well-resourced cyber threat actors, they demonstrate that state of the art (SOTA) models are improving in offensive cyber capabilities. Furthermore, these results represent a lower bound for SOTA models because, as will be discussed below, frontier models, when given the proper scaffolding and tool access, can go much farther.
Taken together, the US National Security Memorandum, real world hacker use of LLMs, and the evaluation results of frontier AI models show that AI is already changing the cyber threat landscape. This has implications for the security of critical infrastructure that modern society relies upon.
Catastrophic cyberattacks against critical infrastructure
Cyberattacks on critical infrastructure have had widely varied effects over the last few decades–with most having little to no impact–but the NotPetya attack stands out as likely the most economically damaging attack. This self-propagating malware deployed by Russian military intelligence against Ukraine in 2017 spread globally to healthcare entities, government agencies, shipping companies, and the energy sector. According to the US Presidential administration at the time, the total economic impact of the data wiper attack totaled more than $10 Billion. No other cyberattack has reached this level of estimated damage.
A catastrophic cyberattack that never actually came to fruition, known as “Nitro Zeus,” presents a second example. In the wake of the 2007 Stuxnet cyberattack against Iranian nuclear weapons production infrastructure, the United States and Iran began multilateral negotiations to put in place restrictions on Iran’s nuclear program. The United States reportedly maintained a contingency plan that consisted of cyberattacks to disable “Iran’s air defenses, communications systems and crucial parts of its power grid” in case diplomacy failed. Such a comprehensive attack, if able to cause communications and electric grid outages for long enough, would have caused likely more economic damage to Iran than NotPetya did to the global economy. Unfortunately, the lack of public details on Nitro Zeus make it difficult to know how developed the contingency attack was or how effective it would have been. Also in this instance, the United States had clear incentives to leak such information to journalists in order to create perceptions in Iran that would strengthen the United States’ hand in nuclear negotiations. This casts doubt on whether the United States had the capability or intention to conduct the attack.
NotPetya’s estimated $10 Billion in damage was significant. But could a cyber attack on critical infrastructure, perhaps one uplifted by highly capable AI models, cause total economic damages an order of magnitude greater ($100 billion) than NotPetya? It is far from trivial for an attacker to cause such massive damage and the attack would need to disrupt critical infrastructure entities at a much greater scale than NotPetya. If the probability of such an event reaches even 1-5% per year, AI labs, cybersecurity innovators, and governments should give even more special and urgent attention to mitigate the risk than they already are.
While there are many critical infrastructure sectors an attacker could disrupt, this analysis focuses on a single example, the energy grid, because so many other critical infrastructure sectors rely on it to function. To that end, this analysis seeks a better technical understanding of just how feasible a cyberattack against the energy grid costing >$100 Billion in damages would be. As shown below, advanced threat actors and nation-states struggle to pull off attacks of much smaller magnitude. The immense difficulty of this attack implies that the AI system involved needs highly sophisticated offensive cyber capabilities to create meaningful attacker uplift. SOTA AI models remain far away from achieving this. However, the rapid advancement of AI capabilities will eventually make the attack more feasible, even if only by a small amount initially. In order to identify and predict the point at which AI systems gain capabilities to make a major electric grid attack more feasible, the attack process itself and all its execution steps must be laid out in as much detail as possible.
Building on Lloyd’s (2015) “Business Blackout” scenario
There are few detailed and rigorous public sources that analyze the technical details and economic consequences of extreme cyberattacks. However, the 2015 report by Lloyd’s and the University of Cambridge’s Centre for Risk Studies stands out as a useful example: Business Blackout: The insurance implications of a cyber attack on the US power-grid.
The report describes a hypothetical cyberattack on the Eastern Interconnection of the US electric grid, which covers the eastern two-thirds of the country, and claims the attack would result in approximately $500 billion of damage. They present three scenarios with differing levels of catastrophic damage but the median scenario includes the following:
- Malware (the hypothetical ‘Erebos trojan’) damages or destroys fifty electricity generators to take down 18,000 MW (10% of total power generation capacity), which in turn triggers a 100% grid failure.
- The report claims it would take up to three days to restore 50% of power and 21 days to restore 90%.
- This prolonged power outage causes $130 billion of direct losses to businesses and households and $544 billion when accounting for indirect macroeconomic consequences over the next five years. The direct effects include damage to electricity assets and infrastructure, loss in sales revenue to electricity supply companies, and direct loss in sales revenue to businesses during the blackout period.
Lloyd’s published the report back in 2015 and future work should revisit their economic calculations. However, the analysis here will take Lloyds’ conclusions as a plausible starting point even if they might suffer from some overestimation.
While the report’s scenario lacks sufficient detail showing how plausible such a consequential cyber attack is, the authors should still be commended for their analytic depth as they sought to tackle a very complex problem. Indeed, the authors do note that:
The attack scenario was designed by subject matter experts and subjected to peer review to ensure that the effects could plausibly be achieved. In the interests of security, we have published only superficial details of the method of attack (which we have given the name the ‘Erebos’ Trojan). This report does not reveal any previously unknown tactics or vulnerabilities.
I also do not want to reveal any previously unknown vulnerabilities. To that end, this analysis draws on several public Industrial Control System (ICS) cyberattack case studies as well as energy grid management literature in an effort to be more concrete and useful for future work. Before getting started, there are some preliminary thoughts worth noting:
- While hackers have been able to physically manipulate critical infrastructure as demonstrated by the Russian Crashoveride attack (treated in detail below), actually damaging the infrastructure with long-term consequences is much more difficult. And when it comes to causing damage to generators, experts seem to disagree on whether this is possible (see the section below on the Aurora attack experiment).
- For damaged generators to cascade into complete grid collapse, many things would have to go wrong. An attacker would have to conduct the attack during a period of high demand and low reserve capacity—and even then, it would require intricacy and coordination.
- Furthermore, it seems very plausible that even if generators were damaged, grid operators could restore power generation from reserves and undamaged components within 24 hours. To create the long-term consequences, the attackers would likely have to engage in psychological manipulation that dissuades grid operators from reconnecting electricity generation and transmission components for fear of further long-term damage.
How does the power grid work?
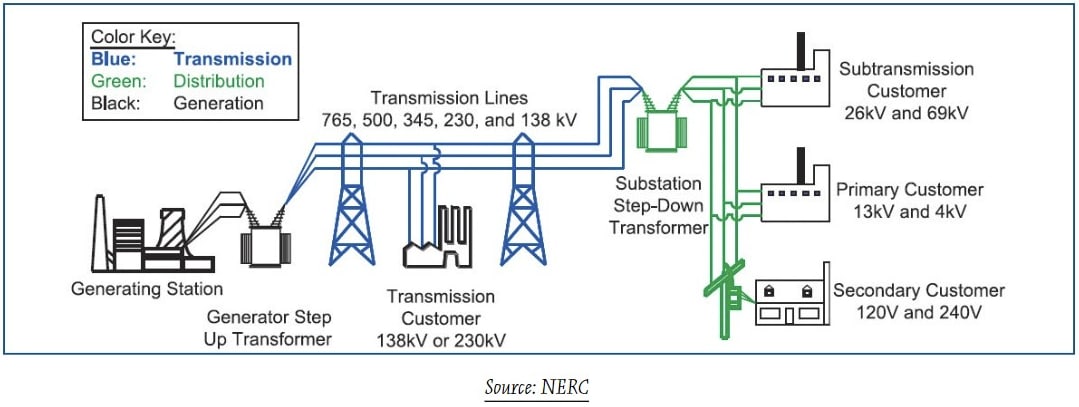
Before delving deeper into an assessment of the attack, a detour into basics of grid operations will set a proper knowledge baseline.
The electric grid consists of three main components. Generation uses coal, natural gas, nuclear, hydro, wind, and solar power plants to produce electricity. Transmission uses high-voltage power lines to send electricity over long distances from power plants to substations. Distribution uses transformers at substations to reduce power to lower voltages and distribution lines deliver electricity to end-users.
Power stability across a wide-area alternating current (AC) grid such as the US Eastern Interconnection requires operators to maintain a sensitive equilibrium between generation and consumption. Electrical grids in the United States rely on a stable grid frequency of 60 Hz. Practically speaking, this means that generators on the grid target and seek to maintain a synchronous rotational speed of 60 times per second. The 60 Hz remains relatively constant if power generation and consumption are in equilibrium. If electricity demand falls, the load on the generators decreases and the rotational speed (frequency) increases. If electricity demand rises, creating more load, the generator frequency decreases as it works harder to keep up.
How could a cyberattack destabilize the power grid?
Cyberattacks in theory can disrupt an electric grid on a large scale in two fundamental ways: 1) blackouts and 2) equipment damage.
First, attackers can turn off generation, transmission, or distribution assets. In order to create cascading blackout effects, the attacker would, by turning off these assets, cause a sudden large imbalance between supply and demand. To maintain stability and protect physical infrastructure from damage caused by overcurrent, voltage deviations, or frequency variations, protective relays in the grid trip to protect equipment when necessary. When these trips occur they abruptly cut off the equipment’s connection to the grid. If the imbalance exceeds the grid's capacity to compensate, a cascading series of relay trips occur, leading to a large-scale blackout. Although disruptive, cascading blackouts are still preferable to equipment damage and can usually be remediated within 24 hours.
Second, attackers can compromise and manipulate grid components like protective relays, generator controls and settings, and transformer substations to create longer-term, physically damaging effects that are not fixable in 24 hours or less. If attackers succeed in damaging or destroying high-voltage transformers or generators, the disruptive effects last longer because these components often cannot be quickly replaced. There is one important caveat here: power generation-as opposed to generators-can be replaced quickly by deploying reserve generation capacity, but the amount of reserve capacity available (which will be treated in detail below) varies based on multiple factors. In fact, unplanned and planned grid component outages are dealt with using reserves all the time. In spite of these reserves, major grid component damage, if inflicted during a time of high demand and low reserve capacity, would still present a problem. Not only are generators and transformers expensive, but they are customized to the operating conditions of the install location and take months to manufacture, meaning there is little to no backup supply. Furthermore, the attack, if executed well, could create conditions in which grid operators fear reconnecting high-voltage transformers and generators to the system because of possible further damage.
How a cyberattack could cause >$100B of damage through destabilization of the power grid: direct and indirect approaches.
The Lloyd’s attack scenario predicts direct economic damages on the order of $100 billion or more but exactly how can an attacker achieve this? Attackers can cause this level of economic damage in two ways: 1) the direct approach: inflict direct damage on just enough equipment to cause grid failure and 2) the indirect approach: leverage the psychological impact of lesser damages to equipment and thereby convince grid operators to keep parts of the grid offline for fear of more damage.
In the direct approach, attackers prevent safety systems, like protective relays, from working properly, then create conditions wherein grid components suffer damage. To cause catastrophic damage to a generator, the attacker would need to render the generator turbine governor ineffective, disable protective relays, and manipulate the breaker that connects it to the rest of the grid. Then the attacker would create a load rejection condition–a sudden loss of demand on the generator–by disconnecting the generator from the grid via its breakers. Repeated connection and disconnection to the grid’s load in absence of proper governor function can apply violent forces on the generator, inducing mechanical failure and destruction.
This attack mimics the Aurora attack test conducted by the US Department of Homeland Security and Idaho National Lab in 2007. The test’s “goal was to produce what is called out-of-phase synchronization (OOPS) by opening and closing the generator’s circuit breaker while it was running and connected to the grid.” When the generator was disconnected from the grid, the electrical load on it decreased dramatically and its operating speed accelerated. Once the generator was reconnected back to the grid without governor protection, it re-accepted the grid load instantaneously, experiencing violent forces as it decelerated. During the test, this repeated disconnection and connection was conducted four total times in less than one minute and caused irreparable damage to the generator.
It is important to note that before the test, all the protective equipment was turned off, making the scenario unrealistic as a demonstration of a real-world attack wherein the hacker would need to stealthily disable the safety equipment first. Furthermore, Dragos–a leading ICS cybersecurity company–questions whether attacking in this way is actually feasible outside of a carefully controlled test. Instead, they state that “a much more effective (if difficult) attack vector lies in modifying breaker logic or functionality to create subtle changes in behavior.” Rather than sending direct commands to abruptly connect and disconnect the generator, Dragos says that manipulating the thresholds at which breakers automatically respond to conditions like load or voltage fluctuations is a more feasible attack. Using this method the attackers could cause immediate damage or damage over time.
The catastrophic 2009 accident at the Sayano-Shushenskaya dam and powerhouse in Russia dramatically illustrates the level of damage a sudden load rejection can have on an improperly governed generator. The day before the accident, a fire at a nearby hydroelectric plant necessitated a large transfer of load to the Sayano-Shushenskaya plant, a load increase that caused the plant to operate beyond its safe capacity. Load in this case corresponds to the total power a generator must produce to satisfy the demand placed upon it. During the hours that preceded the accident, the plant “experienced large and rapid load swings” between 2800 and 4400MW, which to this day lacks full explanation. This was between 43% and 68% of the plant's total 6400MW output capacity. To compensate for the large load swings, the plant operators adjusted the generator governor sensitivity to unsafe levels. They did this because it enabled more rapid control of the hydraulic pressure powering the generator’s rotation in order to adapt its output to the load swings. In response to external conditions that are not fully understood, the over-sensitivity of the governor caused a sudden, violent hydraulic shock as it adjusted the hydraulic pressure on the turbine too quickly in response to a major drop in load. As the plant’s Unit 2 turbine–which also had undermaintained studs holding its head cover on–experienced a sudden total load drop (load rejection), the force of its own inertia essentially blew it apart. The loss of Unit 2 then created a sudden transfer of massive load to Units 7 and 9, causing them to also blow apart. The resulting violent explosion and flooding killed 75 people and destroyed nearly the entire power plant. In summary, this direct approach involves causing major damage to grid components along the lines of the Sayano-Shushenskaya accident to take down electricity generation capacity.
In the indirect approach, attackers cause extended outages through a combination of physical damage and psychological effects wherein grid operators don't want to reconnect components or re-energize the grid for fear of allowing more physical, and therefore, long-term damage. Alternatively, if operators are confused about the problem’s cause or unsure if they have solved it, they would be hesitant to reconnect. This indirect approach will be laid out in detail further down in the attack scenarios section.
Both the direct and indirect approaches require the attackers to compromise grid control systems at scale, though the indirect approach requires smaller scale compared to the direct. Large scale compromise of these control systems is a major reason why such attacks are so difficult and therefore highly improbable. They require successful intrusion into the necessary number of transmission substations stations, generator controllers, protective relays, central control centers, and grid monitoring sensors. If the attackers’ targets are not directly accessible via the open internet, they must intrude into and navigate successfully through the electric utility’s information technology (IT) networks to get to the operational technology (OT) networks and finally to the programmable logic controllers or digital protective relays that directly control the grid. The IT/OT distinction is important here: IT networks generally focus on business operations and communication, while OT networks are focused on controlling physical processes and equipment. OT networks especially ought to be properly segmented and protected from direct exposure to the internet but in practice, many organizations misconfigure and unintentionally expose their OT control systems.
Anatomy of a coordinated grid attack
But how exactly would an attacker intrude into and create physical effects on a fully functioning, protected power grid at the extreme scale in question? Crashoverride–an ICS malware family also known as Industroyer–provides a detailed example of how attackers can compromise and manipulate key grid components, prevent safety systems from working properly, then create conditions wherein grid components suffer damage. In 2016, Russian hackers intruded into an electric grid substation in Ukraine and caused a blackout in Kiev affecting 225,000 people for about one hour. During the initial intrusion, the attackers deployed their ICS specialized malware later nicknamed Crashoverride. After Crashoverride infected the substation OT network it automatically mapped out any control system it could detect and located the specific control systems it was designed to attack. Once it identified its targets–in this case Remote Terminal Units (RTU) communicating with breakers that cut off power transmission–the malware set the breakers to “open” which stopped electricity transmission. Following transmission cut off, Crashoverride “deployed a wiper module to impede recovery and (in this specific case) delete configuration and related files to hamper restoration” on the infected systems. This created a situation in which operators lost visibility and control over the affected equipment, limiting their ability to conduct a coordinated response. The malware then attempted to conduct a denial of service attack (DoS) against the Siemens SIPROTEC protective relays it discovered on the control network by exploiting a known vulnerability, CVE-2015-5374. In this case, the malware “aimed to create an unsafe, unstable condition for reconnected transmission lines at the moment of physical restoration.” However, this step in the attack sequence failed because the malware included poor implementation of the ICS communication protocols and was not able to DoS the protective relays.”
Overall, the Crashoverride “attack sequence sought to de-energize transmission equipment, create a loss of control and loss of view on SCADA systems controlling this equipment, and then aimed to remove relay protection on the de-energized transmission lines.” In response to the outage, crews sent personnel to manually close the breakers at the substation despite not having control visibility into the system. If the protective relays had successfully been made unresponsive to unsafe grid conditions due to the DoS attack, the manual re-energization of the transmission lines could have failed to prevent a dangerous overcurrent condition, causing damage to transformers at the substation. All that said, Russian use of Crashoverride in 2016 can be judged a failure since it only caused an outage in part of Kiev for about one hour and failed to cause any physical damage to transmission equipment. Still, it is worth noting that the malware’s design–the ability to target all relevant control systems on a control network and its ability to easily incorporate communication and control protocols more often used in the United States and Europe–makes it a scalable threat to grids outside of Ukraine.
Looking beyond Crashoverride, what else would the attackers need to accomplish? Past ICS attackers in general have gained initial network access through credential discovery or theft via multiple techniques like password cracking, purchase from the dark web, or social engineering, allowing access to the target systems via abuse of legitimate accounts. It is worth noting that intrusions often rely heavily on these techniques and a grid attack causing greater than $100 billion in damage would need to do the same. In addition to this, the attackers would need to discover and exploit software vulnerabilities unique to each piece of grid equipment. Sometimes the exploited vulnerabilities will provide access to and control over many grid systems over a wide area but in other cases, each OT network would require a unique chain of exploits.
Mass exploitation of a single ICS vulnerability is more feasible than one might think. Many vulnerabilities discovered in recent years affect ICS components that are widely adopted across the electric grid. Two examples among the many thousands illustrate the issue. In 2023, the National Vulnerability Database (NVD) advised that CVE-2022-45789, a vulnerability in Schneider Electric Modicon M340 and M580 programmable logic controllers (PLCs), widely adopted in energy sector applications, allowed an attacker to remotely execute unauthorized Modbus functions on the controller when hijacking an authenticated Modbus session. In 2021, researchers testing the same Schneider PLCs discovered a vulnerability they called ModiPwn that “allows for a complete takeover of impacted devices.” This vulnerability exposed millions of PLCs used widely by energy utilities and other industrial sector users. These examples illustrate well the increased homogeneity in control systems and communication protocols used across the energy grid and other industrial sectors, which enables hackers to scalably attack a greater number of targets using the same exploitation techniques.
Given that many exploits threaten widely adopted ICS components, it seems likely that an attacker would have the advantage of reusing the same exploit to compromise many substations, generator controllers, protective relays, central control centers, and grid monitoring sensors, meaning that the effort required to compromise–as for example in the Lloyd’s report–fifty generators, is not greater than or equal to fifty times the effort of compromising a single generator.
Once the attackers have penetrated far enough into the electric grid control environment, they would seek to understand the grid’s topology, as well as the control systems they must manipulate during the attack. This “prepositioning” process will likely be the longest, most tedious step, one where they will be most in danger of being caught. The attackers would not expect to compromise all relevant grid control and safety infrastructure at once. They would move slowly and deliberately to prevent detection, but the longer it takes, the more likely the operation will be compromised and severely set back.
The attackers would also need to design malware that communicated over multiple separate ICS protocols sending the correct commands to achieve specific, coordinated physical effects. There is precedent for this. Pipedream, a Russia-linked, example of ICS focused malware illustrates how to do it. According to Dragos, the malware, though not known to have been used in a real-world attack, was designed to “disrupt, degrade, and potentially destroy industrial environments and processes.” The analysts found that Pipedream could conduct rapid reconnaissance of ICS/OT networks to discover topology and map the attack surface. According to Dragos, the toolset’s components provide attackers with “an interface for manipulating the targeted devices” that can “execute 38% of MITRE ATT&CK for ICS techniques.”
As the grid attack reaches culmination, a sufficient number of compromised systems must remain compromised by the attackers until execution of the final attack. This number must be higher than the minimally necessary number of systems required for the attack to succeed. Vulnerabilities are discovered and patched regularly, password resets and account changes may remove attacker access, so specialized backdoors that give the attackers persistent and arbitrary access must remain in place without discovery. Crashoverride provides a great example of redundant persistence mechanisms using a dual-backdoor method, allowing “attackers to regain access to a targeted network in case the main backdoor is detected and/or disabled”
In summary, the attackers would need to take the direct or indirect approach while utilizing the complex set of intrusion, persistence, control, and disruption methods above to achieve disruptive effects on the order of $100 Billion in damage.
Three major attack scenarios causing damages on the order of $100B or more become clear based on the two above approaches.
Based on a review of relevant literature, three major attack scenarios present themselves: 1) the Lloyd’s scenario in which the attackers directly damage the minimum correct number of generators, 2) the attackers create a forced oscillation resonance condition that compels grid operators to stop operations, and 3) the attackers conduct a demand-side attack that directly manipulates the demand load placed on the grid. Only the first two scenarios, along with their comparative feasibility and probability, will be treated in depth here.
In the first attack scenario represented by the Loyd’s report, attackers damage 50 generators, which constitutes 10% loss of power generation across the grid. This causes 100% grid failure for three days and 50% failure for another 18 days. At the time of the Lloyd’s report in 2015, the Eastern Interconnection contained “676 generators with capacities above 100 MW and up to 1,400 MW, operating under the supervision of 261 power plants.” Lloyd’s analysis of generator capacity “shows that it would be possible to remove 18,000 MW by taking around 50 generators offline.”
Unfortunately, a lack of specifics in the Lloyd’s report undercuts their conclusions. First let's look at how long it might take to put tripped but not damaged generation systems back online. If the attack causes safety relays to trip fossil fuel steam turbine plants like those that use coal, oil, or natural gas, those resources will resume operations within 18-24 hours according to an electric grid expert. Tripped renewable and gas turbine (as opposed to steam turbine) natural gas fueled generators would come back online very quickly. Total US power generation capacity consists of 43.1% Natural Gas (the vast majority of which falls into the fast recovery category, roughly 90% in 2019) and 21.4% Renewables (also fast recovery). This constitutes roughly 60% of total US generation. Considering these statistics, if protective relays facilitated an interconnection-wide cascading blackout without any damage to grid components, operators under immense pressure to restore power could have electricity restored within one day.
Next consider how long it would take to restore power under conditions where damaged generators required repair or replacement. If the attack successfully damaged more generation capacity than grid operators could replace with reserve capacity, then the percentage of service restored within the 24 hour period mentioned above would amount to whatever generation capacity was left undamaged plus capacity from accessible reserves. Absent other hindering conditions, over 90% of electricity service would be restored within 24 hours given the 10% generator damage number in Lloyd's report. Full restoration would only be complete as repairs or replacements came online. Therefore, it seems incorrect for the Lloyd’s report to claim 10% generation loss alone would lead to 100% grid outage for three days an 50% outage for 21.
Each region of the North American electric grid has different reserve capacity. “Reserve margin” represents a grid region’s ability to generate more power in response to unexpected levels of demand. These margins, a percentage of total generation, vary by region. Regions with reserve margins “less than 15% are considered tight. Those with margins between 15% and 20% are considered balanced, and those with margins greater than 20% are often considered oversupplied.” The North American Reliability Corporation (NERC) publishes a yearly report detailing the reserve margins each region is projected to have under normal, peak, and extreme conditions. Some regions in Canada have projected reserve margins of 19% during extreme conditions. However the MISO region which covers a large portion of the US Midwest has a reserve margin of -6.3% under similar conditions. The WECC-SW region covering Arizona, New Mexico and parts of Nevada and Texas has a reserve margin of -10.8% under extreme conditions. Seven out of the twenty North American regions have reserve margins that indicate “resources will not be sufficient to meet operating reserves under extreme peak-day demand with normal resource scenarios” or “with reduced resources.”
Overall, the NERC report states that these seven regions have potential “for insufficient operating reserves.” This is why the attackers would want to execute their attack during a period of peak demand. Electric grids maintain energy reserves in the form of battery storage, extra generator capacity, compressed air, and water pumped to elevated tanks. In an attack that damages a large number of generators, it should be noted that the reserve margin decreases because damaged generators that might have had reserve capacity no longer contribute.
It’s very difficult to know how the positive and negative reserve margins for each region across an interconnection would net out in the immediate aftermath of the attack but it seems probable that the interconnection would recover to around 90% of full service within one day after fifty generators suffered catastrophic damage. Still, it’s worth noting that Lloyd’s claims three days of total blackout would be driven in part by psychological pressures wherein “utility companies are reluctant to synchronize their facilities to the bulk power system until they understand what caused the generator damage.” However, in the absence of follow-on attacks that reinforce this reluctance, it's hard to imagine that full blackout would persist for three days and 50% power outage for 18 more days. This dramatically undercuts Lloyd’s claims of economic damage on the order of $100 billion. In order to achieve such economic damage laid out in the Lloyd’s scenario, attackers would actually have to damage around 50-60% of generation capacity across the entire Eastern Interconnection, an estimated 400 generators, to achieve outages of 50% for longer than 24 hours. On its face, this seems much harder to pull off. In order to cause a 100% outage for at least three days and 50% outage for 18 more days, the attackers might try a different strategy which will be treated next.
In the second scenario, attackers create a forced oscillation resonance condition. Forced oscillations can have many causes. They occur when a grid system is “excited by an external periodic disturbance from a cyclic load, equipment failure, poor control design, or the mechanical oscillation of a generator during abnormal operation conditions.” Specifically, forced oscillations are equipment induced grid frequency deviations above and below the target 60 Hz of the system. The deviation itself is measured by frequency and amplitude. For example, a forced oscillation could be described as deviating from 60 Hz by a total of ±1 Hz, meaning that it oscillates at an amplitude of ±1 Hz up to 61 Hz and down to 59 Hz. It can also be described as deviating at a certain frequency or rate, such as every five seconds. Researchers at Oak Ridge National Laboratory note that these events “have become a challenging problem with the increasing penetration of renewable and other inverter-based resources (IBRs).” IBRs include solar, wind, and battery storage units. Another study noted that “forced oscillation events are becoming more frequent and more severe.” Furthermore, these events remain a problem despite techniques to dampen them. Because external driving sources, such as malfunctions, cause forced oscillations regardless of system wide damping techniques, they “persist indefinitely until the source is removed by the system operator or protection systems.” Even more concerning, when a forced oscillation interacts with natural oscillation frequencies of a system, it can “propagate across the entire system with highly magnified energy.” This is called a resonance condition.
Multiple severe forced oscillation resonance events have occurred in North America. In January 2019, a 0.25 Hz forced oscillation interacted with the 0.24-0.25 Hz natural oscillation mode for over 18 minutes and subsequently propagated across the entire US Eastern Interconnection. The event originated at a power plant in Florida when faulty equipment caused a generator’s steam turbine valve to open and shut every four seconds. This video illustrates how the event caused oscillations throughout the grid as far away as North Dakota. Another event in November 2005 on the Western Interconnection, originating in Alberta Canada, demonstrates how forced oscillations with an amplitude of 20 MW in resonance with natural oscillations created 200 MW swings at the California-Oregon interface, 1,100 miles away from the source. This is an amplification factor of ten. The resonant amplifications and long distance effects make the source of these events hard to identify. These specific forced oscillation events caused little to no permanent damage and therefore show how the grid remains resilient to events of similar magnitude and duration. Consequently, if forced oscillations represent a plausible catastrophic damage pathway, an attacker must cause an event of greater magnitude and duration than the two above examples.
While not definitively confirmed due to lack of complete information, a forced oscillation event is hypothesized to have played a major role in the 2009 Sayano-Shushenskaya power station accident that destroyed nine of the plant’s ten hydroelectric turbines, killed 75 people, and forced the 6,400 MW plant out of service for three years. The large and rapid load swings that Unit 2 underwent in the hours before the accident are indeed consistent with a forced oscillation.
According to the California Independent System Operator (ISO), an organization that oversees California's bulk electric power system, these events can cause equipment failure, thermal problems, safely relay trips, and automatic generation control issues. Generators specifically, if they are not cut off from the grid by a tripped relay, are most vulnerable to damage if they experience a forced oscillation resonance condition where sudden and large load swings act in opposition to the rotational inertia of the generator’s turbine. In summary, experts agree that these events “pose a permanent threat to the power grid with more than 20 large-scale events in the past 30 years documented in the United States,” some of which still lack “a well-identified root cause.”
Forced oscillation resonance attack
A forced oscillation resonance attack, which would require fewer points of compromise across the targeted grid, has a greater chance of creating economic harm on the order of $100 billion than the Lloyd’s scenario only if the attackers were able to sustain it for longer than three days. Here, the forced oscillation attack’s psychological effects factor into its effectiveness much more. In this second attack scenario, dispersed generators under malicious control together cause a severe forced oscillation resonance condition that propagates across the entire interconnection. Compromised protective relays and safety systems in various strategic locations allow the oscillation to damage other generators and transmission substation transformers. Remaining functional protective relays trip, causing a cascade of blackouts that last for around 24 hours. As the operators work under immense pressure to bring intact grid components and generation capacity back online, law enforcement and cybersecurity threat hunt teams, suspecting a cyberattack, begin to conduct OT network incident response. Even though forced oscillation sources are difficult to detect, the grid operators and threat hunt teams may manage to identify a few compromised generators and successfully remediate some of them. But the second stage of the attack would begin at this point. Late in the 24 hour period after the initial stage, just as most power is coming back online, the attackers, leveraging persistent back doors to compromised generators, create a second severe forced oscillation resonance condition using the generators still under their control as well as reserve compromised generators not used in the initial stage. The effects are repeated, causing a second cascade of blackouts and more damage to grid equipment. At this point, the pressure to speedily reestablish power to the grid is eclipsed by the fear that further attempts will only cause more long term damage to the grid and elongate recovery on the time-scales required to repair or replace failed components. Grid operators and government regulators are forced to muster as many threat hunt teams as possible, go slowly through each grid region’s OT networks and only reconnect each power plant and substation to the grid after full incident response is conducted. All this, of course, is done under rationed electricity conditions while the economy suffers. In order to approach $100 billion in economic losses, this attack fundamentally relies on psychological dynamics of government authorities’ initial under-correction and subsequent over-correction to the threat.
The 2021 Colonial Pipeline incident serves as an example of how an energy sector cyberattack victim responded in a slow, more conservative manner before reestablishing infrastructure operations. In this case, the oil pipeline OT network was not a target of the attack. The ransomware actors only encrypted Colonial Pipeline’s enterprise IT networks. Even though “there was no impact to OT, out of an abundance of caution, Colonial Pipeline still shutdown the OT side of the network,” which stopped fuel distribution. The pipeline remained offline for six days due to the company’s “lack of visibility and understanding of their level of exposure and limited confidence in their ability to mitigate the impact to the OT network.” It seems plausible that the same psychological dynamics in the Colonial Pipeline incident would also hold true during the forced oscillation scenario.
Even though the forced oscillation attack scenario requires compromise of fewer individual electric grid components, thus making it more feasible than compromising and destroying 400 generators, it remains immensely difficult and therefore highly improbable at this time. Furthermore, no public record of a real-world forced oscillation resonance attack makes the scenario highly speculative.
In the third scenario, attackers conduct a “demand side” attack wherein, for example, an “Internet of Things (IoT) botnet of high wattage devices–such as air conditioners and heaters–gives a unique ability to adversaries to launch large-scale coordinated attacks on the power grid” through the direct manipulation of the demand load placed on the grid. This attack will not be assessed in detail here because the number of maliciously controlled IoT devices required to create severe effects across an entire interconnection seems very high, much higher than the 400 generators required in the first scenario.
Out of the three attack scenarios, the forced oscillation resonance attack, seems like the most plausible attack to achieve >$100 billion in direct economic damage.
Unresolved questions
This limited analysis represents a first step in modeling this threat and in no way claims to be comprehensive. Many uncertainties and questions remain, requiring future work to make this threat model clearer and more useful:
- How much damage can a severe forced oscillation resonance condition cause to unprotected transformers and generators? Could an attacker cause such an event? How exactly?
- Have resilience techniques in response to forced oscillations improved? How good are they? How much can they be dampened?
- Is it possible to damage a generator or high voltage transformer enough to take it offline for days, weeks, or months via a cyberattack?
- What is the relationship between the scale of physically damaged equipment and restoration time? Beyond just causing a cascading blackout, how much damage is required to knock out the grid for long enough to cause $100 billion damages?
- Are high voltage transformers and large generators as slow and hard to replace as people say?
- Are generators or high voltage transformers a more promising target for attackers?
- How capable are OT cybersecurity systems? Can they quickly detect and repel such a complex, multistage attack undertaken by a determined and well resourced adversary?
Many more questions beyond these remain. One in particular looms large: how do AI advancements affect all this?
How do increases in offensive AI cyber capabilities affect this analysis?
So far, none of this cyberattack analysis has mentioned AI. But people worried about AI-cyber risk should pay attention because in the last two years, state-of-the-art language models have started to uplift human hacker capabilities. AI models have also shown the ability to conduct offensive cyberattack steps autonomously. When considering cyberattacks on different critical infrastructure sectors, a successful electric grid cyberattack that shuts down an entire US interconnection would be one of the most economically devastating. At this point however, such an attack falls into the category tail risk given its high improbability. But can advancements in AI increase the probability of such an attack by a factor of five or ten over the next several years? Several major contributing factors like past attacks and current AI capabilities determine the probability that this attack will occur. Past attempts to breach and disrupt electric grids like Crashoverride and the Volt Typhoon campaign, have caused little to no disruption. Crashoverride caused an outage for one hour and failed to do physical damage. The Chinese Volt Typhoon campaign conducted extensive cyberespionage operations against critical infrastructure in Europe, the Pacific, and the United States but caused no disruptions or damage. The attacks detailed above are highly complex, requiring expertise, time, and resources. Relevant AI capabilities, which will be treated below, provide meaningful attacker uplift but not enough to move the needle at this time. Given all this, the probability remains extremely low, possibly 0.1–1% per year, based on an informed subjective guess. However, given how much AI capabilities have developed recently, this estimate could increase rapidly and unexpectedly. Within just the last two years, SOTA AI models have demonstrated increased cyberattack capabilities such as attack resource development, gaining initial target access, post compromise network discovery and lateral movement, and overall attack autonomy. Examples of each of these will be treated in detail.
Autonomy
Researchers leveraging a team of Large Language Model agents have recently demonstrated the LLMs’ ability to conduct multiple stages of a cyberattack independently when given access to a deterministic graph of attack tactics, techniques, and procedures (TTPs). The graph of TTPs provides the LLMs a set of attack methods that they must reason over, follow, and remain constrained by. Constraints like this direct LLMs and help overcome their tendency to get sidetracked by their own mistakes. These researchers constructed an LLM-based “automated end-to-end attack construction and emulation system” called AURORA (not to be confused with the Aurora test above). This system processes cyber threat intelligence (CTI) “reports to generate an attack plan based on the attack procedure knowledge graph. It also constructs the necessary infrastructure for attack emulations. By leveraging LLM, AURORA analyzes attack knowledge from various sources and organizes multiple attack procedures into a comprehensive full-life-cycle cyberattack. The evaluation results demonstrated that AURORA can construct a full-life-cycle attack and the required infrastructure from a report in several minutes without human intervention.” When they tested it, they found that “considering the connections between attack procedures” represented in a graph improves the attack “success rate by 28% (from 79/163 to 125/163).”
Researchers at an AI offensive security startup called XBOW conducted an evaluation comparing their LLM system with human pentesters on a set of pentesting challenges. XBOW pitted five different human pentesters, all with differing levels of expertise ranging from junior to world class expert against their AI system. According to their results the expert “pentester and XBOW scored exactly the same, namely 85%. The staff pentester scored 59% success. If all human pentesters are taken together as a team, they solved 87.5% of challenges, only slightly more than XBOW on its own. A big difference is in the time taken. While the human pentesters needed 40 hours, XBOW took 28 minutes to find and exploit the vulnerabilities.” Here, the speed advantage of the AI system over humans is very impressive. AI hacking speed, when paired with ever increasing offensive technical capability, will likely have a profound effect on the cyber threat landscape, necessitating the development of comparably fast defensive solutions.
It is extremely important to note that LLMs perform best in autonomous offensive cyber hacking situations when they have a scaffold [LW · GW] built around them. An LLM scaffold is a system that wraps a structure of useful tools around a core LLM and chains together multiple LLM prompts to perform more complex tasks using those tools than a single prompt can achieve. It is similar to providing a human hacker with a set of offensive tools and allowing the human to reason about how to use those tools. Evaluations of LLMs without scaffolding often elicit less impressive cyber offensive capabilities. For example, research done by Meta that did not leverage scaffolding showed that “that both novices and experts using the [Llama] 405B model demonstrated insignificant uplift over having open access to the internet without an LLM.
Resource Development: attackers gather and develop tools and capabilities required to conduct an attack.
In a somewhat limited fashion, attackers can use AI models as instructors or tutors to plan and execute stages of a cyberattack. Attackers that lack certain expertise in areas like OT communication protocols, ICS controller capabilities, exploit writing, or active directory exploitation can gain meaningful understanding by querying LLMs, which have been trained on vast amounts of relevant cyberattack data. One significant limitation attackers face when employing this strategy is that, for attacks on ICS/OT, LLMs likely lack enough detailed knowledge of the inner workings of controller hardware and software or detailed schematics and specifications of energy grids because those details are often held close by entities who manufacture and run the systems. This means that the LLMs are likely not trained on high volumes of this data. Until LLMs are trained on such data, they will be of limited use in conducting effective and sophisticated attacks on an energy grid. However, well-resourced nation-state cyber actors can afford to purchase these systems and train LLM augmented offensive cyber tools on the relevant ICS/OT data. Once SOTA models are trained on or given access to this exquisite data, they will speed up the reconnaissance phase of an ICS cyberattack, allowing the attacker to quickly understand the nuances of the target network’s attack surface and inner workings. But this doesn’t mean a less well resourced attacker can’t still use existing LLM knowledge to uplift their ICS attack capabilities. For example, an ICS cybersecurity expert was able to use the free version of ChatGPT to recreate the Russian ICS Malware tool called Frosty Goop, which attacked an energy company in Ukraine, resulting “in a two-day loss of heating” for 600 households. The expert fed a Dragos report on the malware to Chat GPT and asked it to create usable code to mimic the described malware capabilities. Chat GPT complied and generated the code, which replicated Frosty Goop’s ability to communicate over Modbus TCP to achieve OT impacts.
Initial Access: attackers successfully breach the target network.
SOTA models have shown the ability to find and exploit software vulnerabilities. Google Project Zero researchers tested state of the art LLMs’ ability to conduct Advanced Memory Corruption and Buffer Overflow vulnerability discovery. The researchers were able to 20x the success rate on buffer overflow discovery and 3x the success rate on Advanced Memory Corruption discovery on the “CyberSecEval” model evaluation suite compared to tests done by Meta on the same evaluation suite. Another group of researchers showed that “teams of LLM agents can exploit real-world, zero-day vulnerabilities. Prior agents struggle with exploring many different vulnerabilities and long-range planning when used alone.” To improve capability, they created “a system of agents with a planning agent that can launch subagents. The planning agent explores the system and determines which subagents to call, resolving long-term planning issues when trying different vulnerabilities.” They constructed “a benchmark of 15 real-world vulnerabilities” and showed their system improved prior work by 4.5x.
Discovery and Lateral Movement: attackers search the target network for sensitive information or other weak points to gain greater access.
Offensive security researchers from the startup Dreadnode built a scaffolded LLM to leverage a well-known hacker tool called “Bloodhound” to conduct network discovery and lateral movement actions. The scaffolded LLM conducts queries against Microsoft Active Directory to enumerate the relationships between users, servers, and groups. Then it identifies which relationships among these entities are exploitable for deeper target network access. These, “post-compromise” actions are crucial steps an attacker must take to achieve their overall attack goals and require reasoning that thinks through multiple steps in advance.
Defense Evasion and Stealth
One crucial capability that LLMs have not been evaluated extensively for is their ability to conduct attacks that leverage stealth and defense evasion against a network with defensive capabilities in place like endpoint detection and response (EDR), security event and incident management (SEIM) systems, and a security operations team. For complex, lengthy, and high stakes offensive cyber operations, stealth and defense evasion play an outsized role. The lack of exploration in this area should inspire researchers and model evaluators to create benchmarks and evaluations to measure this.
Conclusion
The above is an enumeration of just some of the ways attackers can use SOTA models to achieve a desired impact on a target network. These advancements improve the capability of novice and intermediate hackers by enabling them to use techniques they were previously incapable of, helping them to learn faster. The most talented and well resourced hackers will gain uplift by directing teams of autonomous hacking agents, increasing the scale and speed of their attacks. Still, despite these demonstrated offensive cyber capabilities, the probability of a successful attack that brings down an entire electric grid interconnection, even if uplifted by current SOTA AI, remains extremely low, <1% per year. But rapid or sudden advancements in AI capabilities, which we now have precedent for, would force an update to this probability estimate.
0 comments
Comments sorted by top scores.